So in This Blog we Understanding Linux File and Directory Permissions. A good Linux user must understand the basic file and directory permissions because that will help him keep his system safe and open. And whether you are a beginner in Linux or have long been using it, this piece of information is a must-know. In this tutorial, you will learn the basics of file and directory permissions and how to set permissions with some advanced ways of controlling access to your files and directories
Summary Key Takeaways
- Understand permissions on Linux file and directories
- Learn reading permission strings and how access can be managed for the user, group, and others
- Understand concept of ownership of files and how change it
- Know SUID, SGID, Sticky Bits
- Learn the Power of Access Control Lists.
Basic Concepts of Linux File Permissions
For our start with Linux file permissions, we need to know the basics. We will consider how users, groups, and others could use files and directories. We’ll be covering file types, how they are represented in terms of their permissions, and the three main categories of access.
File Types and Permission Notations
Linux supports a variety of file types. Two of the most common are regular files and directories. Each has its own permissions set up in terms of access. Letters such as “rwx” indicate read, write, and execute.
Understanding Permission Strings
A permission string for a file or directory contains 10 characters. The first character is a letter, defining the file type, while the rest identify whether he or she is permitted to read, write, or execute. These apply for user permissions, group permissions, and read/write/execute permissions.
User, Group, and Others Categories
- User: This file owner has the maximum privilege
- Group: His belonging group may have extra permission privileges.
- Others: they also don’t own or are of that group and have permissions too.
These basics of Linux file permissions are essentials in managing your system. Knowing these, you can handle file access much better. In this way, user permissions, group permissions, and read/write/execute permissions are all right.
It’s how you keep your system, really learning about Linux permissions with regard to file and directories.
Understanding Linux File and Directory Permissions
Learning about Linux file and directory permissions is key to managing your system well. We’ll explore the permission system and what each character means.
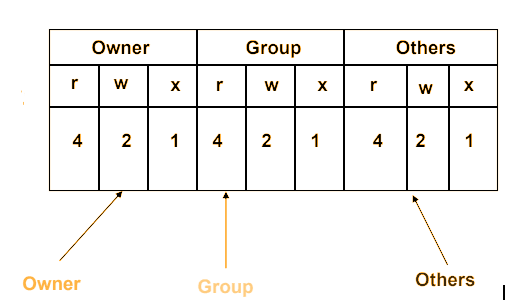
Linux prints out permissions to file or directories in ten characters. The first tells us the type of the file. The remaining nine give information about reading, writing, or execution privileges
- The first group (characters 2-4) represents the owner’s permissions.
- The second group (characters 5-7) represents the group’s permissions.
- The third group (characters 8-10) represents everyone else’s (others) permissions.
| Character | Meaning |
|---|---|
| File Type | ‘-‘ for regular files ‘d’ for directories ‘l’ for symbolic links ‘c’ for character devices ‘b’ for block devices ‘p’ for named pipes ‘s’ for sockets |
| User Permissions | ‘r’ for read ‘w’ for write ‘x’ for execute ‘-‘ for no permission |
| Group Permissions | Same as user permissions |
| Other Permissions | Same as user and group permissions |
Example -rwxr-xr– it means that one file contains the following type of permission:
- User can read, write, and execute.
- Group can read and execute.
- Others can only read.
Knowing about permissions helps you manage access. It ensures the right permission representation and character meaning in your Linux system.
File Ownership and Access Control
File permissions of Linux are more than the just read, write, and execute. It also talks about ownership and ACL. We will find all those important elements regarding management files and directories of Linux as we proceed ahead in the article.
Ownership for Users and Groups
Every file and every directory in Linux has an owner and a group owner. The user owner can control the file most thoroughly. The group owner will identify who in a group has access to it. Information on ownership is fundamental for you to manage your Linux resources’ access.
Changing Ownership of Files with chown
The chown command changes the user and/or group ownership of a file or directory. It is a very important tool in giving people proper access to your system’s resources. You use chown to control the ownership of files and files contained in directories when you want to protect important data.
Setting Group Permissions with chgrp
The chgrp command is able to change the group ownership of a file or directory. This is pretty useful if you want to share files or directories with groups rather than changing access permissions for users one by one. Handling ACLs for groups is really what makes your Linux environment very flexible and secure.
In the following section, some advanced concepts of permission evolve with SUID, SGID, and Sticky Bits.
With this, you will become well-equipped to understand what access control in Linux in terms of files and directories is.
Advanced Permission Concepts: SUID, SGID, and Sticky Bits
There are the three main concepts under Linux, which are setuid, setgid, and sticky bits. These are forms of special permissions controlling which file to access by whom. These three bits enable our Linux systems and also ensure more security.
The setuid bit allows a user to run a file with the same permissions that the file’s owner owns. It is just good for those tools that need a little extra access, like a password manager or system tools.
The setgid bit makes a file or directory belong to the group of the parent directory. It’s useful for groups working together, where everyone needs to edit shared files safely.
The sticky bit on a directory forces you not to delete a rename files unless you have rights to do so with them as owner, group of the directory owner and as root. It comes into use on public space as /tmp so all deleted files are not found when you want to modify one
Knowing how to make the most of these enhanced permissions is important for securing your Linux system and making it clean. Using setuid, setgid, and sticky bits, we can make our systems pretty useful and protect all that is of utmost importance to us.
Working with Access Control Lists (ACLs)
ACLs are one of the primary means of file control under Linux. They tend to help in the improvement of further control of who may read, write, or delete what. The ACLs can provide information to us that the traditional permission system cannot provide us with.
Implementing ACLs on Files
To use ACLs on files, we can make use of the setfacl command. This lets us give certain permissions to users or groups. For example, we can let some users read a file but not write or run it.
Managing Default ACLs
We can also set default ACLs on directories. It means that the new files or directories within that directory get the same permissions. It makes managing large file systems easier.
ACL Best Practices
- Keep good records of your ACL settings for consistent access control.
- Check and update your ACLs often to remove old or unnecessary permissions.
- Use the umask setting to set default permissions for new files and directories. This helps with your ACL setup.
Learning to use Access Control Lists well can make Linux file management better. It helps us make our system more secure and easy to use for everyone.
Conclusion
Linux file and directory permission is basically one of the essentials for keeping your system safe. It helps you control access to your files and other resources. We have been learning the basics and their application in controlling permissions.
We have understood how to set the permissions for users, groups, and others. And also the advanced topics like SUID, SGID, and Sticky Bits add more security and control to it.
Now we know how to secure our Linux systems by controlling ownership of files and use of Access Control Lists (ACL). Really, following best practices keeps our data and systems from unauthorized access.





